penetration testing thick client applications|thick client checklist : discount store Discover what thick client penetration testing is and learn how it is conducted. Uncover vulnerabilities and protect your systems effectively with BreachLock. Celebrity exposed in Brasil Leaks nude pussy porn Fodadospacks. Brasil nudez yaskara kellen uma linda morena brasileira. Teen Brasilian exposed beautiful home New Fodadospacks. . Brasileira photos & videos. EroMe is the best place to share your erotic pics and porn videos. Every day, thousands of people use EroMe to enjoy free photos .
{plog:ftitle_list}
web29 de mar. de 2023 · Contribua com o canal: https://livepix.gg/lima112-----Arquivos do vídeo:OP.
1. Capturing the request via Echo Mirage. Echo Mirage enables intercepting non-HTTP traffic between the tested thick client and the local or remote server. Intercepting requests using this tool, give insight into what kind .
What is a Thick Client Application? Difference Between Thick Client and Thin Client Application. Understanding Thick Client Application Security Testing. Types of Thick Client Penetration Testing. 1. Data .
web penetration testing checklist
thick client pentest checklist
In this article, we will learn about thick client applications, their vulnerabilities and ways to carry out security assessment of these applications. A thick client, also known . Discover what thick client penetration testing is and learn how it is conducted. Uncover vulnerabilities and protect your systems effectively with BreachLock.Identifying and exploiting vulnerabilities within the thick client application itself, such as insecure configurations, input validation flaws, or logic errors, is crucial in penetration testing. Thick client (Desktop) application penetration testing is the process of evaluating the security of a thick client application by simulating attacks to identify vulnerabilities.
Thick client (Desktop) application penetration testing is the process of evaluating the security of a thick client application by simulating attacks to identify vulnerabilities. A thick client application, also known as a fat client , is a software program that runs on a local machine and communicates with a server or a database to perform its . Thick client application penetration testing entails studying the application’s business logic to find and correct any weaknesses that might be used to jeopardize the system’s operation. 10. Data Tampering. Thick client .This course introduces students to the penetration testing concepts associated with Thick Client Applications. This is an entry level to intermediate level course and we encourage you to take this course if you are interested to learn Thick Client Application Security. Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. This phase aims to identify communication protocols and potential entry points for exploitation.
Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities in applications that run on client devices, such as desktops or mobile. Conclusion. This blog highlights different tools and approaches for testing a thick client application for vulnerabilities. The tools have remained the same over a period of time and there are no major changes in the way thick client applications have been assessed when compared to web / mobile applications, where introduction of new frameworks / technologies . Understanding Thick Client Penetration Testing. Thick client penetration testing is a proactive approach to evaluating and enhancing the security of applications that run locally on a user’s device.
Discover hidden vulnerabilities in windows thick client applications! Master thick client pentesting with our comprehensive course. Learn thick client pentesting tools, methodologies and exploits - enroll now! . Enrol on a thick client penetration testing course to get an insight into the thick client penetration testing methodology. Learn .Our team of experts conducts thorough penetration testing for web, mobile (Android/iOS), APIs, and thick client applications, minimizing the risk of breaches.Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses.
Thick Client Penetration Testing aims to assess and ensure the secure deployment of thick client or native applications by simulating real-world attacks and analysing potential weaknesses. This comprehensive testing process helps uncover critical vulnerabilities that could be exploited by malicious actors, ensuring that the application’s .A practical guide to pentesting thick client applications. . Thick Client Application Penetration Testing Course Introduction Course Introduction (1:37) Help and Support Downloadables Introduction and Lab Setup Introduction to Thick Client Applications (4:12) Lab Setup - Part 1 (2:04) Lab Setup - Part 2 (18:44) . Discover the importance of Thick Client Penetration Testing to safeguard your application. Learn how RSK Cyber Security protect your business. . At RSK Cyber Security, we offer complete thick client application penetration testing services to help organizations secure their thick client applications. Our expert team conducts thorough . In this series of articles, we will learn various tools and techniques used to perform thick client application penetration testing. A step by step breakdown being deployed, we will discuss about starting with the very basics to the advanced test cases. Introduction . Referenced under multiple names, such as: Fat client/Heavy client/Rich client .
thick client penetration testing methodology
Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different . Thick Client Application Penetration Test: What It Is and How to Do It. Thick client penetration testing is a security assessment process that focuses on identifying and mitigating vulnerabilities .Learn practical thick client application penetration testing techniques. How to reverse engineer .NET binaries. Students will learn how to patch .NET binaries. How to identify and exploit common security issues in 2-tier applications. Learn multiple ways to intercept TCP traffic coming from thick client apps. If a thick client application has a built-in feature to set up a proxy server, then it is known as a proxy-aware Thick client. Testing these types of thick clients is easy and straightforward due .
Thick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and prioritize remediation efforts to mitigate cyber risks. Memory analysis is crucial in penetration testing thick client applications. It involves examining the contents of computer memory when the process is running, which can disclose sensitive information like usernames, passwords, session tokens, secret keys, etc.
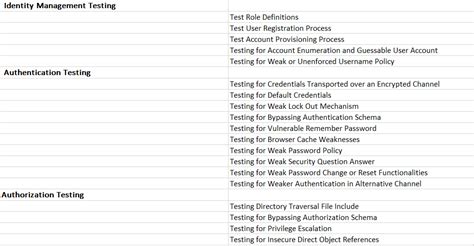
GUI TESTING. Test For GUI Object Permission. Display hidden form object; Try to activate disabled functionalities; Try to uncover the masked password; Test GUI Content. Look for sensitive information; Test For GUI Logic. Try for access control and injection-based vulnerabilities; Bypass controls by utilizing intended GUI functionality; Check .
Common examples of thick client applications are video games, audio video editing tools, Microsoft Office, etc. Thick client security assessment can be divided into below four major parts. Static test In the rapidly evolving landscape of cybersecurity, organizations face an increasing challenge to secure their software applications and protect sensitive data. Among the arsenal of defense mechanisms, penetration testing, or "pen testing," has emerged as a vital practice to identify and mitigate vulnerabilities. In this article, we delve into the fascinating world of thick . While testing thick client applications is crucial, it comes with unique challenges: . Best Practices for Thick Client Penetration Testing. To overcome challenges and ensure effective security . Thick client penetration testing is an important task that needs to be done with every thick client application because thick clients have two attack surfaces first one is static and the other one .
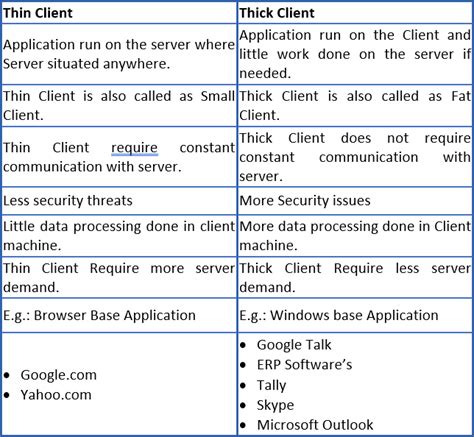
A thick client, also known as a fat client or rich client, is a software application that performs most of its operations locally on the user’s device. This includes data processing, storage . Importance of Pen Testing Thick Client Applications. Because thick client apps provide special security issues, pen testing is essential. Moreover, thick clients manage complicated functions and sensitive data while running on users’ devices. Hence, they are often the focus of cyberattacks. Penetration testing is necessary to find .
thick client penetration testing checklist

thick client checklist
thick client application testing
penetration testing checklist
Resultado da 5 dias atrás · Encontre dicas de apostas para os principais jogos de futebol que acontecem neste dia para os mercados 1x2, over/under, handicap e demais mercados. Compartilhamos as previsões, estatísticas, comparamos as equipes e as chances para os principais mercados do jogo para que .
penetration testing thick client applications|thick client checklist